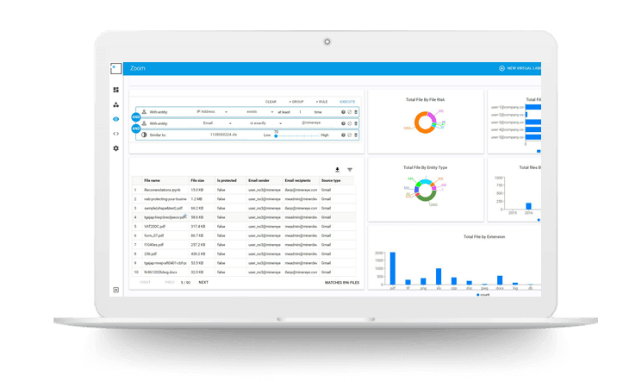
Reporting the results of a data breach to regulators and customers is a slow and uncomprehensive process with potential penalties, brand damage and customer attrition. With little visibility into its dark unstructured data, organizations leave its PI and sensitive data exposed to hijacking or leakage. As regulatory bodies mandate fast reporting and granular data handling, organizations require an automated unstructured data discovery tool to mitigate the negative effects of a data breach, and to foresee breach potential on a continuous basis.


Continuously scans a terabyte of data per hour for sensitive information, using AI and machine learning to adapt to changes in form and files, discovering PI and business entities within images, attached files, PDFs, Office, text/CSV and binary data. Applies a risk score to every file for clear-cut prioritization.