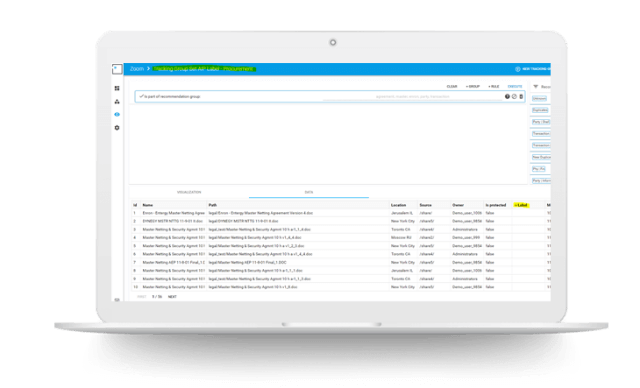
The radically increased use of cloud-based collaborative platforms has resulted in a massive uncontrolled sharing of business critical and sensitive personal (PI) data. Countless mistakes and legacy labeling and policy enforcement tools leave organizations’ sensitive data unprotected and mishandled. Organizations require tools to synchronize their security, privacy and business goals within the file labelling process. Accurate labels are applied according to the relevant policy, the user, file content, and context of use. The label is constantly updated automatically and deployment of the tool is fast and simple.


Leverages AI and ML to scan 1 TB of data in an hour in a variety of dimensions, e.g. meta-data, content, risk, location, permissions. Puts a risk score to every file for clear-cut prioritization of mitigation.